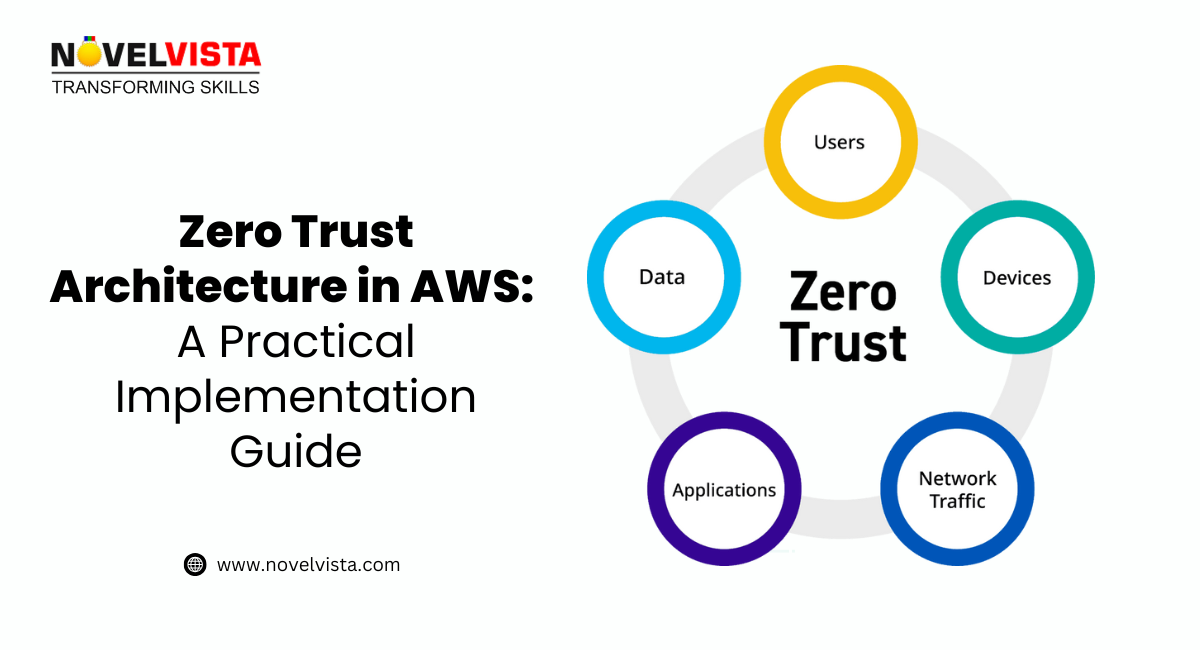
With today's more distributed and hybrid workplaces, organizations have to contend with the escalating challenges of cybersecurity. Conventional security models, with the perimeter being the main emphasis, are not enough to secure organizations from sophisticated attacks. Meet Zero Trust Architecture (ZTA), a contemporary security model that presumes no trust—within or outside the network—and insists on ongoing validation for everyone, devices, and systems.
AWS, with its vast ecosystem of security services, provides a robust platform for implementing Zero Trust Architecture. Whether you’re running a cloud-native application or a hybrid environment, AWS offers the tools, services, and best practices to support a zero-trust approach. This blog will take you through the key elements of Zero Trust, how to apply it in AWS, and offer real-world examples, best practices, and FAQs to assist you in establishing a robust security posture for your business.
5W + How Framework for Applying Zero Trust in AWS
Who Should Apply Zero Trust in AWS?
Primary Users:
- Cloud Security Teams: Responsible for safeguarding cloud-based workloads and data.
- DevOps and system Teams: Governance of infrastructure as code (IaC) and automated deployment while protecting microservices, containers, and applications.
- CISOs and Compliance Teams: Implementing that security frameworks such as Zero Trust fit the compliance and regulatory needs of the organization.
- Security Architects: Creating network security designs, imposing segmentation, and providing identity-based security controls.
Example
A bank implements Zero Trust in AWS to protect its customer-facing applications and back-end infrastructures. They utilize AWS services like IAM, VPC, and AWS SSO to impose strict access controls so that only allowed users and devices can have access to sensitive financial information.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a cybersecurity strategy that believes no one, both within and outside the network, should be trusted as a default. Access is only given after ongoing verification of identities, devices, and network health. It comprises:
- Micro-segmentation: Segmenting the network into smaller areas to restrict the horizontal movement of attackers.
- Least-Privilege Access: Providing users and devices with access only to the resources they strictly require.
- Continuous Monitoring and Authentication: Employing constant monitoring and real-time access controls to evaluate risks.
Zero Trust in AWS can be achieved through the implementation of multiple security services that concentrate on identity, monitoring, encryption, and access control. These services assist in maintaining strict verification at each step and preventing implicit trust from being provided.
Example
A medical organization implements Zero Trust with AWS so that only legitimate medical staff can see patient information, even when working in the same organization. With AWS IAM for fine-grained access control and Amazon VPC for micro-segmentation, the organization assures that sensitive information is isolated from unauthorized access.
When to Apply Zero Trust Architecture?
Zero Trust must be applied when:
- Managing Sensitive Information: If your company organizes and processes sensitive information like personal health records (PHI), financial data, or intellectual property, Zero Trust is a must.
- Securing Distributed Workforces: With remote or hybrid workers, remote access to resources must be secured from anywhere.
- Enabling Legacy Infrastructure Modernization: Companies moving to the cloud or blending on-premises resources with cloud services must use Zero Trust to secure hybrid environments.
- Preventing Lateral Movement: If your company is interested in preventing laterally moving attackers in the network, micro-segmentation and tight access controls must be applied.
Example:
A multinational corporation with a massive hybrid infrastructure deploys Zero Trust throughout AWS and on-premises data centers. They utilize AWS Transit Gateway to bridge their on-premises networks to AWS VPCs, using micro-segmentation by security groups and enforcing tight access controls using AWS IAM.
Where to Apply Zero Trust in AWS?
Zero Trust can be applied in AWS in the following elements:
- Identity and Access Management (IAM): A core part of the Zero Trust framework, IAM allows you to enforce least-privilege access policies so only approved users access certain resources.
- Virtual Private Cloud (VPC): VPC lets you contain network traffic from various zones and apply segmentation to control communication across them.
- AWS PrivateLink and Transit Gateway: Both services enable private connectivity between on-premises networks and VPCs, so data is never exposed to the public internet.
- AWS Identity Federation and Single Sign-On (SSO): Utilized for centralized user management and authentication, so access is always checked.
- AWS Web Application Firewall (WAF): Guards applications against known threats like SQL injection and cross-site scripting (XSS).
- AWS CloudTrail and GuardDuty: Offer auditing and continuous monitoring to ensure that everything happening in the environment is logged and processed for malicious behavior.
Example:
An insurance firm utilizes IAM for hard access control within its cloud infrastructure. They set up AWS WAF to secure public-facing applications, use GuardDuty for threat intelligence, and audit all activity with CloudTrail in real time.
Why Use Zero Trust in AWS?
Adopting Zero Trust Architecture within AWS guarantees:
- Reduced Attack Surface: Micro-segmentation and least-privilege access stop lateral attacker movement.
- Ongoing Risk Assessment: AWS offers real-time monitoring and auditing tools so that all actions are logged and risk-analyzed.
- Regulatory Compliance Standards: Zero Trust enables organizations to comply with strict regulatory and compliance standards like PCI DSS, HIPAA, and GDPR by imposing strong access controls and ongoing monitoring.
- Fewer Insider Threats: By making continuous verification and segmentation mandatory, Zero Trust reduces the likelihood of insider threats and hijacked accounts.
Example:
A government organization deploys Zero Trust across its AWS environment to secure sensitive data about citizens. By using AWS IAM for identity management, AWS CloudTrail for logging, and AWS KMS for encryption, they keep data secure and tightly controlled access.

How to Implement Zero Trust in AWS
To implement Zero Trust in AWS, one needs to combine multiple AWS services to apply strong identity and access management, network segmentation, encryption, and constant monitoring. The following are the major steps to follow to apply a real-world Zero Trust Architecture in AWS:
Step 1: Identity and Access Management (IAM)
- Apply MFA (Multi-Factor Authentication): Enforce MFA on all users, particularly for accessing sensitive resources.
- Deliver Detailed IAM Policies: Utilize AWS IAM policies to grant users and services access to the resources they require (least privilege).
- Enable Identity Federation: Integrate with external identity providers (e.g., Active Directory, SAML) to safely manage access and authentication.
Step 2: Network Segmentation with VPC
- Create Isolated VPCs: Utilize Amazon VPC to segment sensitive resources into private subnets and apply security controls.
- Use Network ACLs and Security Groups: Use network access control lists (NACLs) and security groups to closely manage inbound and outbound traffic between services.
- Use AWS PrivateLink: Utilize PrivateLink for private AWS services and on-premises resource access without publicly exposing them.
Step 3: Safeguard Application Access with AWS SSO
AWS SSO for Focused Access Management: Apply AWS Single Sign-On (SSO) for focused verification of users, providing users access to only required resources.
Step 4: Continuous Observing and Logging
- Enable AWS CloudTrail: Utilize CloudTrail to track API calls and monitor activity in your AWS environment.
- Activate AWS GuardDuty: Continuously observe AWS environments for harmful behavior and risks.
- Use AWS Config: Observe changes in your AWS environment and enforce compliance policies.
Step 5: Encrypt Data in Transit and at Rest
Use AWS KMS for Key Management: Use AWS Key Management Service (KMS) to securely manage encryption keys.
- Secure Data at Rest: Safeguard all data in S3, EBS, and RDS using AWS KMS-managed keys.
- Encrypt Data in Transit: Use SSL/TLS to encrypt data in transit, such that communication between clients and servers happens over an encrypted connection.
Example:
A multinational retail company adopts Zero Trust through the use of AWS IAM for user access management, VPC for segregation of systems, AWS SSO for authenticating users, AWS KMS for encryption, and GuardDuty for threat detection. Their design makes it so that all systems are constantly monitored and any malicious behavior is instantly addressed.
Real-World Use Cases
Use Case 1: Zero Trust for a Healthcare Platform
-
Challenge: A healthcare provider must ensure HIPAA compliance and safeguard sensitive patient information while providing collaboration across multiple departments.
- Solution: The provider controls access to patient information using AWS IAM, applies MFA to sensitive systems, and encrypts all health records with AWS KMS. AWS GuardDuty is turned on to continuously monitor and network segmentation is achieved through Amazon VPC.
- Outcome: The healthcare platform meets HIPAA compliance, has safeguarded access for medical professionals, and safeguards sensitive information at all times.
Use Case 2: Zero Trust for a Financial Institution
- Challenge: A financial institution must protect financial transactions and sensitive customer information, with no trust extended to any user or service by default.
- Solution: The organization accepts Zero Trust with IAM policies applied with least-privilege access, safeguards financial information in transit and at rest with AWS KMS, and uses AWS CloudTrail for end-to-end logging and auditing. Further, AWS WAF is rolled out to safeguard web applications.
- Outcome: The financial institution improves its security posture, ensure regulatory compliance, and minimizes data breach or unauthorized access risk.
Frequently Asked Questions (FAQs)
1. What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture is a security framework that presumes nobody, both inside and outside the organization, is to be trusted by default. All requests, both internal and external, are to be verified and authenticated in real-time.
2. What AWS services enable Zero Trust?
Major AWS services that enable Zero Trust are IAM, VPC, AWS SSO, AWS GuardDuty, CloudTrail, and AWS KMS for encryption.
3. How does AWS IAM enable Zero Trust?
AWS IAM facilitates fine-grained access control by enabling you to specify who can access certain resources and services, following the principle of least privilege.
4. Is Zero Trust a total solution for cloud security?
Zero Trust is a good security model, but it needs to be supplemented with other AWS security services such as CloudTrail, WAF, and GuardDuty to ensure complete protection.
5. Can I apply Zero Trust to an AWS/on-premises hybrid environment?
Yes, AWS services such as AWS Direct Connect, AWS VPN, and AWS Transit Gateway enable you to apply Zero Trust to extend to hybrid environments.
6. How do I audit activity within a Zero Trust environment?
Use AWS CloudTrail to record all API calls and AWS GuardDuty to identify potential threats. AWS Config assists you in maintaining compliance by monitoring configuration changes.
7. Must Zero Trust involve a full overhaul of my current architecture?
Although Zero Trust might need substantive revisions to your security policies and access controls, it is not necessarily a total rebuild of your infrastructure.
8. What are the primary challenges in implementing Zero Trust in AWS?
Primary challenges include maintaining consistent enforcement of security policies, identity, and access management across multiple services, and the integration of Zero Trust principles with existing systems.
9. How do I automate AWS Zero Trust implementation?
You can use Infrastructure-as-Code (IaC) such as AWS CloudFormation, Terraform, or AWS CDK to automate the deliveries of Zero Trust principles such as VPC segmentation and IAM policy.

Conclusion
Zero Trust Architecture is an important solution for securing cloud environments, particularly in AWS. With AWS's extensive collection of security services, you can establish continuous authentication, safeguard sensitive data, and adhere to compliance mandates.
Ready to deploy Zero Trust in your AWS environment?
Let us speak with you today on how to roll out a Zero Trust Architecture suitable for your organization!
Author Details

Mr.Vikas Sharma
Principal Consultant
I am an Accredited ITIL, ITIL 4, ITIL 4 DITS, ITIL® 4 Strategic Leader, Certified SAFe Practice Consultant , SIAM Professional, PRINCE2 AGILE, Six Sigma Black Belt Trainer with more than 20 years of Industry experience. Working as SIAM consultant managing end-to-end accountability for the performance and delivery of IT services to the users and coordinating delivery, integration, and interoperability across multiple services and suppliers. Trained more than 10000+ participants under various ITSM, Agile & Project Management frameworks like ITIL, SAFe, SIAM, VeriSM, and PRINCE2, Scrum, DevOps, Cloud, etc.
Confused About Certification?
Get Free Consultation Call