- What is ISO 27001 for Businesses?
- Benefits of ISO 27001 Certification
- Comprehensive Implementation Guides
- Methodologies for Implementation: PDCA Cycle
- Roles and Responsibilities in ISO 27001 Implementation
- Understanding Annex A Controls in ISO 27001
- Common ISO 27001 Implementation Difficulties and Solutions
- Providing Long-Term Sustainability: Obstacles to Maintaining Compliance with ISO 27001
- Sustainability techniques in long term
- Workable Approaches to Successful ISO 27001 Implementation: Doable Measures to Overcome Obstacles
- Final Thoughts
What is ISO 27001 for Businesses?
The most well-known standard for information security management systems worldwide is ISO 27001. It outlines the specifications an ISMS must fulfill.The ISO 27001 standard offers guidelines for creating, implementing, maintaining, and continuously improving an information security management system for businesses of all sizes and across all industries. The latest version of ISO 27001 is 2022. Explore theISO 27001 Certificationfor more details.When an organization or corporation complies with ISO 27001, it indicates that it has implemented a risk management system for the protection of its data and that the system adheres to all of the best practices and principles outlined in this international standard. It isbeneficial for businessesin different ways.
Let's discuss what are the problems that organizations face during the implementation of ISO 27001?
1. Lack of Top Management Support
Probably one of the most significant challenges to implementing ISO 27001 is establishing and maintaining top management commitment. Information security tends to be thought of as a matter of technology or operation, which is not relevant to strategic concerns. As a consequence, very little interest may arise from top management. The lack of their support makes it quite difficult to secure resources and priority for the project.
Strategy to Overcome:
Such top management commitment can be gained if the benefits are communicated in their language: reputational protection, competitive advantage, and avoiding the costly impact of data breaches. Demonstrating how information security underpins business objectives will move the dial on the perception of ISO 27001 from a simple compliance exercise to a business-value-added activity.
2. Understanding the requirements of the Standard
ISO 27001 consists of an entire standard with various aspects of information security. To individuals who are new to these, requirements therein may sound overwhelming. Misconceptions about them can result in improper implementation.
Strategy to Overcome:
First, train all those involved in the implementation. You may want to engage a consultant who has experience with ISO 27001 to help your team understand what the standard requires. Secondly, break down the standard into smaller areas and concentrate on one area at a time. In doing so, you will not be overwhelmed by the volume of work. You can even use gap analysis tools that allow you to compare what you are doing at the moment against the requirements of the standard, and then focus on closing those gaps.
3. Resource Allocation
Implementation ofISO 27001involves huge investments in terms of time, money, and human resources. Most of the businesses lack the resources to be spent in abundant measures due to their small or medium size with a constraint on budgets.
Strategy to Overcome:
Effective planning is the means to manage resources for the implementation of ISO 27001. Come up with a detailed plan that has all the tasks involved, timelines, and resource requirements. This plan should be quite realistic; based on your current workload of your team. If this is a budget constraint, then implement the standard in phases. Address the most critical areas first.
4. Cultural Resistance
Since new processes and controls are introduced by ISO 27001, there is likely to be some employee resistance. The employees will definitely resist such changes since they feel it is something additional, inconsequential, or burdensome if they do not understand why the change in them has to be effected. It will, in turn, slow down the implementation process and ultimately affect the successful functioning of ISMS.
Strategy to Overcome:
While implementing ISO 27001, change management is necessary. Create awareness in all employees about information security and how it benefits the organization. Engage the employees by seeking their inputs and addressing their concerns. Obvious communication and training will help to take out mystique from the change and make them feel more involved.
5. Documentation of the ISMS
The most logical methodology of approach in this regard is to attain documentation for policies, procedures, and records in compliance with the requirement of ISO 27001. For most organizations, creating and then maintaining the documentation can be rather challenging, more so if they lack some experience in writing such documents.
Strategy to Overcome:
The secret to adequate documentation is to keep it simple and relevant. It means really focusing on what's needed to meet the requirements of the standard, while eschewing excessive documentation that will ultimately be a burden. To help get you started there are templates and guides available. Not to mention document management software to keep your ISMS documentation in line.
6. Risk Assessment Challenges
Risk assessment is a portion of ISO 27001 that involves the implementation of controls, which requires an organization to identify and estimate risks that might compromise information assets. It is, however, a step that most organizations cannot, or even struggle to, accomplish because they either lack the requisite skills or find a sufficiently precise risk analysis very challenging.
Strategy to Overcome:
A risk assessment requires a structured approach. First, identify your information assets and the vulnerabilities and threats applied against such assets. On completion of the previous step, assess their impact or probability of occurrence.If you are unsure how to proceed, consider using risk assessment tools or seeking guidance from an experienced consultant. Regularly reviewing and updating your risk assessment is also essential, as the risk landscape can change over time.
Benefits of ISO 27001 Certification
Obtaining an ISO 27001 Certification provides numerous advantages:
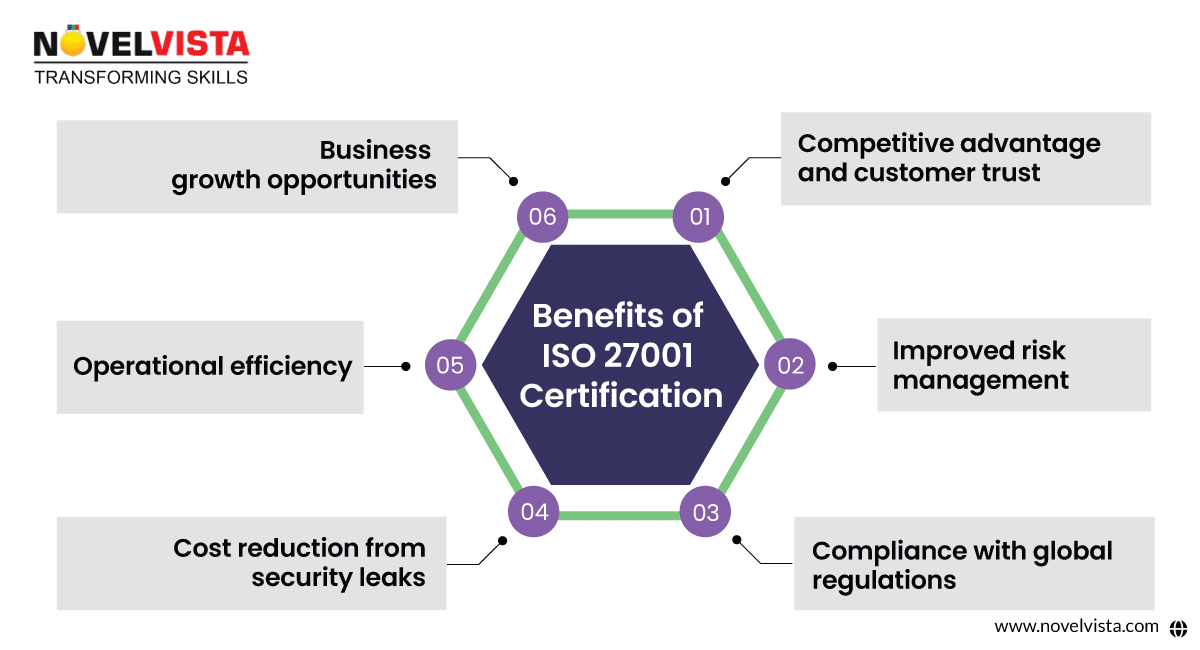
1. Competitive Advantage and Customer Trust
- Certification enhances credibility and assures clients of data protection best practices.
2. Improved Risk Management
- Helps businesses with ISO 27001 risk mitigation by proactively identifying and mitigating threats.
3. Compliance with Global Regulations
- Assists in meeting legal requirements like GDPR, HIPAA, and CCPA.
4. Cost Reduction from Security Leaks
- Make security stronger, minimizing possible financial losses from cyberattacks.
5. Operational Efficiency
- Standardizing policies through ISO 27001 implementation eliminates redundancies and streamlines security processes.
6. Business Growth Opportunities
- Many industries require certification for vendor partnerships, opening doors to new contracts.
Comprehensive Implementation Guides
Successfully implementing ISO 27001 requires a structured approach that ensures a smooth transition from planning to certification. Organizations need a well-defined roadmap to navigate compliance challenges effectively.
Step-by-Step Implementation Process:
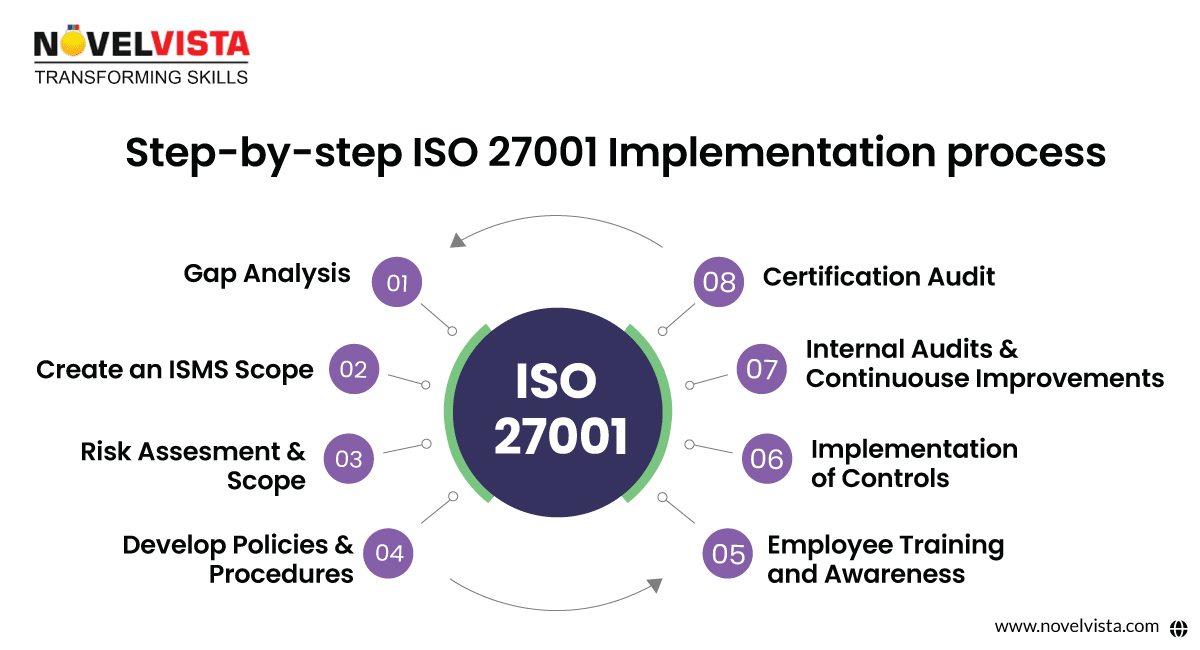
- Gap Analysis: Assess your current information security posture against ISO 27001 requirements. Identify missing controls and areas for improvement.
- Create an ISMS Scope: Set the boundaries of your ISMS framework best practices, covering assets, departments, and processes.
- Risk Assessment and Treatment: Identify vulnerabilities, assess threats, and determine appropriate risk mitigation strategies.
- Develop Policies and Procedures: Create security policies covering security controls in ISO 27001, including access control, encryption, and incident response.
- Employee Training and Awareness: Perform security awareness programs to guarantee compliance across the organization.
- Implementation of Controls: Deploy the necessary security and administrative controls aligned with ISO 27001 implementation requirements.
- Internal Audits and Continuous Improvement: Conduct regular audits to identify compliance gaps and implement corrective actions before the external audit.
- Certification Audit: Connect an accredited certification body to conduct the final audit and grant the ISO 27001 Certification.
Methodologies for Implementation: PDCA Cycle
A widely used approach in effective ISMS implementation is the Plan-Do-Check-Act (PDCA) cycle:
- Plan: Identify security risks, establish ISMS objectives, and define security policies.
- Do: Implement security controls and processes.
- Check: Analyse and measure ISMS performance through audits.
- Act: Implement corrective actions and continuously improve security measures.
Roles and Responsibilities in ISO 27001 Implementation
A successful ISO 27001 Lead Auditor implementation requires a well-coordinated team to ensure compliance and effective execution.
Key Stakeholders Involved:
- Top Management: Assure strategic coordination and resource distribution.
- Information Security Officer (ISO): Leads the process, conducts risk assessments, and manages ISMS.
- IT Team: Implements technical security controls in ISO 27001 and oversees network security.
- Department Heads: Ensure security policies are enforced within their teams.
- Employees: Must stick to the security protocols and follow ISMS guidelines.
A well-structured team ensures seamless ISO 27001 adoption and minimizes implementation hurdles.
Understanding Annex A Controls in ISO 27001
Annex A of ISO 27001 provides security controls in ISO 27001 to help organizations manage security risks effectively. These controls fall into four major categories:
1. Organizational Controls (A.5 - A.18)
- Policies, leadership commitment, and risk management practices.
2. People Controls (A.6 - A.8)
- User verification, training programs, and access control methods.
3. Physical and Environmental Controls (A.11 - A.13)
- Securing facilities, frameworks, and physical access points.
4. Technological Controls (A.14 - A.18)
- Data encryption, secure software development, and incident response methods.
Companies should embrace relevant security controls in ISO 27001 depending on their risk profile and business requirements.
Common ISO 27001 Implementation Difficulties and Solutions
Many organizations face difficulties with ISO 27001 implementation, but these can be overcome with proactive measures.
1. Resource Allocation
- Challenge: Limited personnel and budget limitations slow down implementation.
- Solution: Secure top management support by demonstrating how ISO 27001 adoption mitigates risks and enhances business value.
2. Employee Training and Awareness
- Challenge: Resistance to new security policies.
- Solution: Perform regular training, ISO 27001 Certification Course Training, and security drills to assure compliance.
3. Documentation Complexity
- Challenge: Maintaining extensive security documentation.
- Solution: Use templates and automation tools to simplify policy management.
4. Overcoming ISO 27001 Audit Challenges
- Challenge: Meeting compliance requirements for certification audits.
- Solution: Perform regular internal audits, find solutions for non-conformities, and document corrective actions to ensure a smooth ISO 27001 Lead Auditor review process.
By addressing these challenges, organizations can streamline their effective ISMS implementation process.
Providing Long-Term Sustainability: Obstacles to Maintaining Compliance with ISO 27001
Even if businesses successfully implement the practices of ISO 27001, maintaining adherence might be more difficult than anything on this list. A non-conformity-shaped spanner in the works can be brought into play by many factors—some of them quite ordinary—others not so much: a change in technology, workforce turnover, evolving risks and laws, declining stakeholder participation.
Sustainability techniques in long term
Businesses should have routine audits aside from rigorous monitoring of the procedures, guidelines, and ISMS you have implemented on a day-to-day basis. Engage stakeholders; staff as much as possible to create a security culture and allow for the embracing of newly released technology appropriate in nature.
Workable Approaches to Successful ISO 27001 Implementation: Doable Measures to Overcome Obstacles
The general steps that shall be taken while dealing with any matter pertaining to the compliance of ISO 27001 are as follows:
- At the very outset, set up a good team and stay together.
- Carry along the stakeholders, management, and other staff from the beginning.
- Listen to any advice, comments, questions, and feedback.
- Proper records of your journey to compliance should be maintained.
- Keep yourself open to change and willing to adjust your approach if required.
- In a nutshell, implementing ISO 27001 is not an easy journey.
However, by understanding these challenges and applying practical strategies to overcome them, organizations can successfully achieve certification and, more importantly, enhance their overall information security posture.Remember that the key to success lies in preparation, engagement, and a commitment to continuous improvement. In adopting a proactive approach, facing the challenges, and dealing head-on with issues, your organization will surge down the path to implementing ISO 27001 confidently and leverage a robust ISMS.
Final Thoughts
As we read above, businesses should get ISO 27001 certification. Grasp the above details carefully since it is not only going to help you enhance your practices but also will let you explore its benefits. Therefore, implement ISO with strong practices which will help businesses gain success in today's competitive market.
Managing ISO 27001 implementation difficulties may seem challenging, but ISO 27001 Certification Course Training and proper planning can simplify the process.
Whether you aim to improve data security, elevate compliance, or gain a competitive advantage, ISO 27001 remains the gold standard in effective ISMS implementation. By resolving risks, overcoming ISO 27001 audit challenges, and implementing security controls, businesses can build a tough ISMS that confirms long-term compliance and resilience.
Is your organization ready to take the next step toward ISO 27001 certification? Secure your future today with NovelVista!
Ready to Overcome ISO 27001 Implementation Challenges with Confidence?
Get certified and equip yourself with the knowledge to tackle real-world obstacles in information security management.
Author Details

Mr.Vikas Sharma
Principal Consultant
I am an Accredited ITIL, ITIL 4, ITIL 4 DITS, ITIL® 4 Strategic Leader, Certified SAFe Practice Consultant , SIAM Professional, PRINCE2 AGILE, Six Sigma Black Belt Trainer with more than 20 years of Industry experience. Working as SIAM consultant managing end-to-end accountability for the performance and delivery of IT services to the users and coordinating delivery, integration, and interoperability across multiple services and suppliers. Trained more than 10000+ participants under various ITSM, Agile & Project Management frameworks like ITIL, SAFe, SIAM, VeriSM, and PRINCE2, Scrum, DevOps, Cloud, etc.
Confused About Certification?
Get Free Consultation Call









