- What is ISO/IEC 27001, & Why Does It Matter?
- What is an ISMS?
- Why Should You Care About ISMS?
- Why Does Risk Management Matter in ISMS?
- Key Components of Risk Management in ISMS
- Risk Management Challenges in ISMS
- Best Practices to Ensure Effective Risk Management in ISMS
- A Simple Guide to ISMS Framework
- How to Implement ISO 27001 – Step-by-Step
- Key ISO 27001 Policies You Need
- What Happens in an ISO 27001 Audit?
- Future Outlook: Holistic Risk Management
- Statistics
- Conclusion
What is ISO/IEC 27001, & Why Does It Matter?
Think of ISO 27001 as your business’s security playbook. It tells you what to protect, how to protect it, and how to prove you’re doing it right.
Quick Breakdown of ISO 27001:
- Purpose– A structured approach toinformation security management, helping businesses safeguard sensitive data.
- Structure– 10 core clauses + Annex A, which includes 93 security controls (passwords, firewalls, access control, etc).
- Key Areas– Focuses on risk monitoring, vulnerability management, and incident response.
Want to master ISO 27001 auditing? Check out ourISO 27001 Lead Auditortraining program.
What is an ISMS?
An ISMS refers to the set of policies, procedures, and controls that an organization implements to manage the risks associated with its information security. ISO/IEC 27001 is an international standard which explains how to manage security risks in terms of information. It provides steps and guidelines to help organizations protect their data in an organized way.
ISO/IEC 27001 is not just about preventing attacks but also focuses on understanding and proactively managing risks in a structured way. The ISO 27001 helps organizations identify possible attacks to their information and take preventive measures to control them before they turn into an issue. This approach ensures that security isn't just reactive but part of a well-organized, ongoing process. A key question that arises from this is that: Why is risk management so important within the Information Security Management System (ISMS) framework? AnISO 27001 coursecan answer this question. We can explore how effective risk management builds a strong, reliable, and efficient ISMS.
Why Should You Care About ISMS?
So, why go through all the trouble of setting up this framework? Because security isn’t just about stopping hackers—it’s about building trust, staying compliant, and keeping operations smooth. Here’s what you gain:
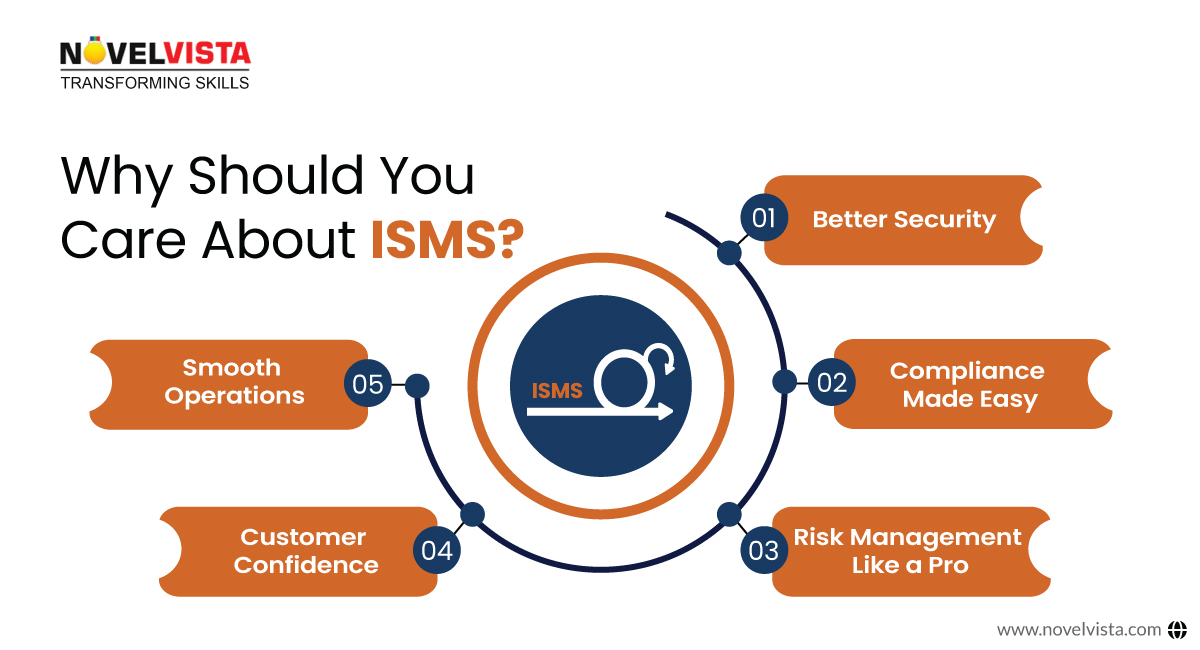
Better Security
Say goodbye to weak spots! This framework helps you identify and fix security gaps before they become problems.
Compliance Made Easy
Whether it’s ISO 27001, GDPR, HIPAA, or others, an ISMS keeps you on the right side of the law.
Risk Management Like a Pro
With proper risk management, you’ll know exactly where your most significant threats are—and how to handle them.
Customer Confidence
An ISMS boosts your reputation and gives you a competitive edge. Remember, clients love businesses that take security seriously.
Smooth Operations
A structured ISMS framework keeps things running efficiently. It prevents Security issues that can lead to downtime and losses.
Why Does Risk Management Matter in ISMS?
Risk management in the ISMS framework is not only mere identification of threats but finding out how to understand and mitigate any potential impact that such risks will generate in the organization. Hence, risk management is viewed through the prism of the ISMS. The primary questions it essentially answer is:
- What could go wrong?
- What are the chances of that occurring?
- If it occurs, what would be the impact of it?
This means that risk management enables an organization to:
- Identify vulnerabilities:To understand which systems, data, and processes are vulnerable.
- Determine possible threats:To estimate how likely it is that those risks become real-life problems.
- Develop mitigation strategies:To use controls or actions to reduce the possible impact those risks may have.
This systematic process allows businesses to be relevant while threats continue to evolve and adapt always holding the position to be ahead in this digital world.
Key Components of Risk Management in ISMS
Risk should be a complete understanding on which a robust ISMS is built. While it is true that the ISMS framework provides structure, without risk management, it would not be effective.
The following are some of the key components of the risk management in ISMS:
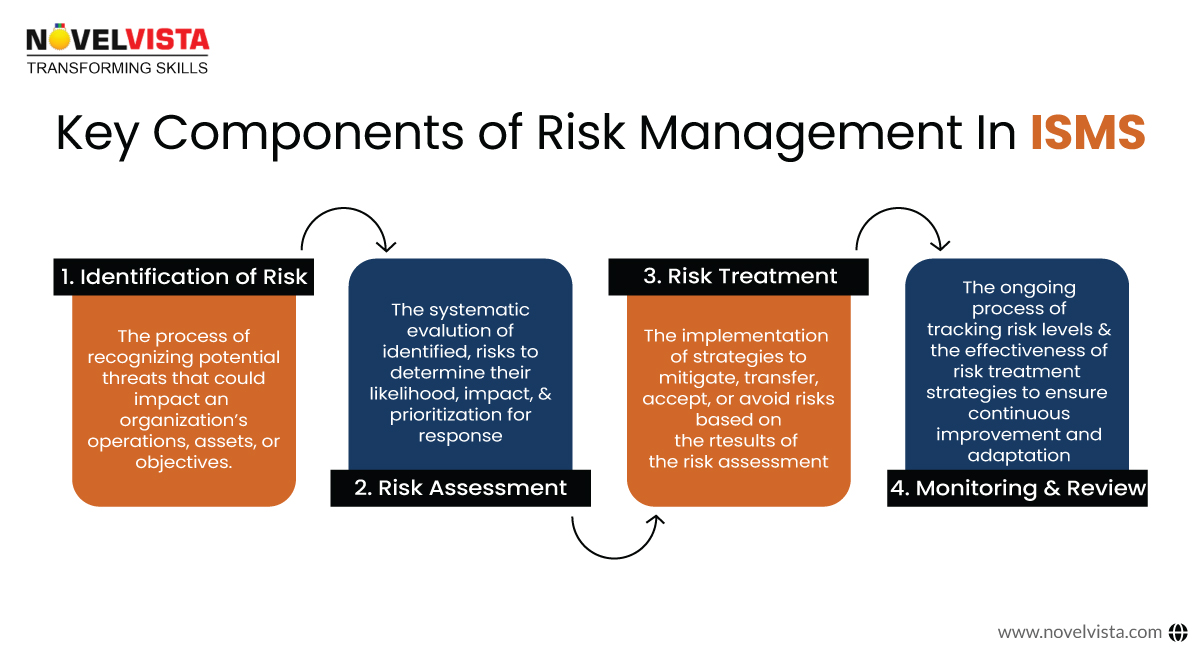
Identification of Risk
Risk management involves both identifying and handling the risks. It?s about knowing the possible dangers or attacks that could harm an organization?s information security beforehand. Internal threats may include employees mishandling of data, while external threats may come from external cyberattacks. This means that identifying risks is almost equivalent to conducting audits in organizations to discover weaknesses ranging from system failures to human errors and external attacks. By understanding what threats can be caused, one can take the preventive measures to lay the foundation for how to tackle these issues and protect the organization.
Risk Assessment
The next thing is to evaluate the risks after they have been identified. In this regard, after identifying every risk, an individual must analyze every identified risk concerning the possibility of it happening with an organization and the consequences likely to result from its occurrence. Risk assessment helps in identifying which threats need to be addressed immediately and which can be monitored over time. This process allows an organization to prioritize its responses to potential risks, focusing on the most critical issues while keeping an eye on less urgent ones. For example, a cyberattack may be very likely and have a high-impact consequence, while a limited system failure might be less likely and have a lower impact. By comparing risks in this way, organizations can prioritize and allocate resources to the most critical areas.
Risk Treatment
Once identified and evaluated, one needs to know how to handle those risks. Hence, the process of selecting and implementing measures which reduces or mitigates the exposure to risks is called risk treatment. One example of this is strengthening cybersecurity measures or providing education on best security practices.
Some of the common ways of dealing with risk treatment include:
- Avoidance:Eliminating the cause of the risk to prevent it from happening.
- Mitigation:Taking steps to reduce the chances of the risk occurring or its impact.
- Transfer:Shifting the risk to someone else, like outsourcing or buying insurance.
- Accept:Acknowledging the risk but deciding not to act on it, especially if it has a low chance of happening or a minor impact.
Monitoring and Review
The management of risks is never static. Nowadays, new dangers that had not existed before appear, while relatively low-priority risks become serious over time. This is why monitoring and reviewing the risks in the ISMS are a continuous need today. Ordinary audits and assessments through penetration testing will put the risk management plan into effect from time to time.
Risk Management into ISMS Policy Integration
It is to be noted that risk management does not stand alone but rather can integrate very deeply into the overall framework of ISMS. The policies and procedures of ISMS are based on the findings from the risk assessments. For example, once it has been determined that there is a risk in the system, a policy might well be formed to ensure that certain safeguards are placed in the system.
For example, consider control over access as if access without authorization is a severe threat according to the risk assessment, then ISMS policies could well be determined to include controls to address that risk, such as two-factor authentication (2FA) controls, controls to limit access to sensitive information and controls for regulated password change requirements. In other words, the success of an ISMS is highly dependent on continuous alignment with risk management and security policies. If this is not integrated, then the organizations are likely to implement policies that may not address the most significant threats they face.
Risk Management Challenges in ISMS
Risk management is quite vital within the framework of an ISMS, yet it brings along its own set of challenges. Some of the common obstacles organizations face include the following:
Changing Risk Environment
The major challenge here is the dynamic nature of the threat. New vulnerabilities could arise with technological changes, so it becomes challenging to stay ahead. Therefore, updates in the ISMS should be an invariable process, and risk assessments should be made regularly for continuous improvement and upgrading in this regard.
Cost as Compared to Security
Risk mitigation comes with a cost. For most organizations, achieving a high level of security requires financial investment. Spending on controls that don?t target the most critical risks can waste resources, while insufficient investment leaves the organization exposed to potential threats.
Human Factor
Human error will always be one of the biggest risk factors, no matter how advanced the ISMS is. Employees may unknowingly expose some information, fall for phishing attacks, or mishandle sensitive data. Therefore,ISMS trainingand awareness programs are always important to minimize such human risks.
Complexity of Compliance
In highly regulated industries such as banking or healthcare, additional complexity would be introduced in terms of incorporating regulatory compliance with one or more laws (for example, GDPR, HIPAA, or CCPA). In those cases, the risk management should ensure that the organizational practice meets not only the threat mitigation but also ensures alignment with the laws.
Best Practices to Ensure Effective Risk Management in ISMS
To ensure that risk management efforts within the ISMS framework would be effective, organizations can adopt several best practices:
It is important to instill a risk-based thinking mindset so that managing risk becomes part and parcel of everyday decisions and does not just boil down to a single exercise. Risk awareness should be the culture of an organization, not merely an exercise.This must regularly execute risk assessments and threat evaluation to identify new risks or changes in existing threats.
- Incident response planning:Maintain an incident response plan. A strong set of best practices helps to manage the risks, but something will go wrong and bad things will happen no matter how hard you might try not to let that happen. Preparing for the unexpected mitigates the impact of the incident and also minimizes disruption to operations.
- Employee Training:Keep your employees trained on current security best practices and information risks to mitigate the human factor in information security. For this one can rely on theISO 27001 certificationcourse, which keeps the employees updated and provides a structured approach to managing and protecting sensitive information, reducing the risk of data breaches and security incidents.
- Inter-departmental Cooperation:The risk management practice should be collaborative. Departments must collaborate to gain an appreciation of the various business areas that can potentially be at risk.
A Simple Guide to ISMS Framework
It is a term for structured security systems that keep your organisation’s data safe. Think of them as a blueprint for cybersecurity. Different industries use different frameworks, but here are the top three you should know:
- ISO 27001– The gold standard! It focuses onrisk assessmentand security policies to protect your data.
- COBIT– It helps businesses align security with operational goals, Ideal for IT governance.
- NIST SP 800-53– Packed with detailed security controls, mainly used by government agencies.
Each framework helps organizations prevent breaches, manage security risks, and comply with regulations. Choosing the right one depends on your industry, risk level, and compliance needs.
How to Implement ISO 27001 – Step-by-Step
Want to get ISO 27001 certified but don’t know where to start? Here’s a simple roadmap to guide you:
- Kickoff Meeting– Define your goals, scope, and team members for the project.
- Risk Evaluation– Identify security risks, vulnerabilities, and their impact.
- Create Policies & Controls– Develop clear guidelines for security framework implementation and data protection.
- Apply Security Measures– Implement risk control measures, encryption, and access controls to safeguard data.
- Employee Training– A system is only as good as its users! Teach your team security best practices to prevent errors.
- Internal Audit & Fix Gaps– Check for weak spots, address issues, and strengthen your framework.
- Certification Audit– Once everything’s in place, an external auditor will assess your system and grant certification.
Want to ace the process? Join ourISO 27001 Certification Courseand get expert guidance!
Key ISO 27001 Policies You Need
To stay compliant with ISO 27001, businesses need clear security policies defining their risk and data protection approach. Here are some must-haves:
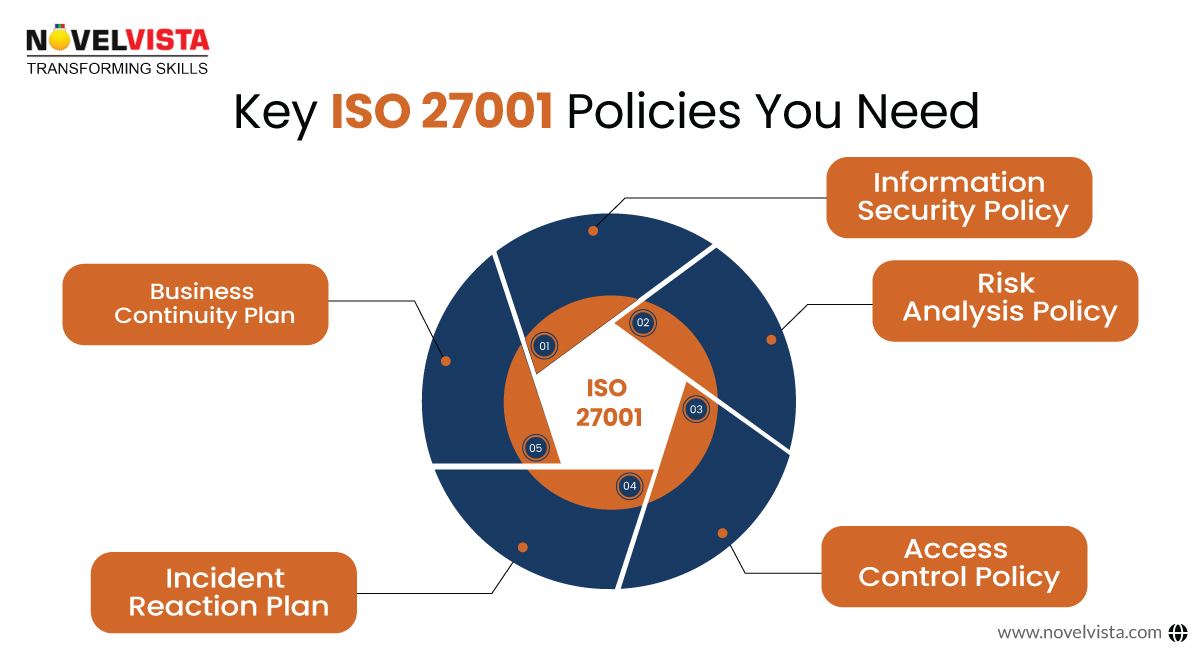
Essential Policies:
- Information Security Policy– The foundation of your ISMS, outlining security objectives and responsibilities.
- Risk Analysis Policy– A plan to identify, evaluate, and mitigate threats.
- Access Control Policy– Defines who can access what, preventing unauthorized data exposure.
- Incident Reaction Plan– Steps to follow in case of a security breach.
- Business Continuity Plan– Ensures your company stays operational during cyber incidents.
Not sure how to create these policies? Learn with our ISO 27001 Certification Course!
What Happens in an ISO 27001 Audit?
Getting ISO 27001 certified means passing an audit—but don’t worry, it’s just a structured review to ensure your security measures are solid. Here’s what to expect:
- Pre-Audit Check– Your team conducts an internal audit to fix any gaps before the official review.
- Stage 1 Audit (Document Review)– The auditors check yoursecurity best practices, policies, and procedures.
- Stage 2 Audit (Implementation Review)– They test how well your risk monitoring, vulnerability management, and incident reaction plans actually work.
- Audit Findings– Any issues? You’ll get a report highlighting areas for improvement.
- Certification Award– If you pass, congrats! You’ll receive ISO 27001 certification.
Want to ace your audit? Join our ISO 27001 Lead Auditor training and become an expert!
Future Outlook: Holistic Risk Management
In a nutshell, risk management is at the very core of a successful ISMS. It ensures proactive identification, assessment, and mitigation of risks for an organization's information security strategy to stay strong and adaptive. Risk management is an ongoing process that involves periodic reviews, updates, and a sharp sense of the changing threat landscape.
An organization taking a holistic approach which integrates risk management with an evolving ISMS framework stays alert to emerging threats and fosters a culture of security-conscious decision-making even better placed to protect its information assets while simultaneously preserving the trust that customers, partners, and stakeholders have in the same. Long-term security and resilience cannot be in any better hands.
Statistics
Researchshows that 41% of firms have reported three or more major risk occurrences. This figure demonstrates the substantial effect of risk occurrences on companies and the significance of effective risk management techniques.
Conclusion
An ISMS framework is more than just a set of rules—it’s your organisation’s security game plan. It helps you stay ahead of threats, manage risks smartly, and keep your data safe. ISO 27001, as offered by training providers likeNovelVista, isn’t just about ticking compliance boxes; it’s about building trust, preventing cyberattacks, and ensuring smooth operations
Think of it like this: Would you rather react to security threats when they happen or prevent them in the first place? A solid ISMS lets you do just that. Every step you take, from risk assessment to incident response, strengthens your defence.
So, why wait? Start your ISO 27001 journey today and take control of your organisation’s security—before a hacker does!
Author Details

Mr.Vikas Sharma
Principal Consultant
I am an Accredited ITIL, ITIL 4, ITIL 4 DITS, ITIL® 4 Strategic Leader, Certified SAFe Practice Consultant , SIAM Professional, PRINCE2 AGILE, Six Sigma Black Belt Trainer with more than 20 years of Industry experience. Working as SIAM consultant managing end-to-end accountability for the performance and delivery of IT services to the users and coordinating delivery, integration, and interoperability across multiple services and suppliers. Trained more than 10000+ participants under various ITSM, Agile & Project Management frameworks like ITIL, SAFe, SIAM, VeriSM, and PRINCE2, Scrum, DevOps, Cloud, etc.
Course Related To This blog
ISO 27001 Certification & Training in the Philippines
Confused About Certification?
Get Free Consultation Call









