
Cloud security is the highest priority in AWS. When you host your environment in the cloud, you can be assured that it’s hosted in a data center or in a network architecture that’s built to meet the requirements of the most security-sensitive organization. Additionally, this high level of security is available on a pay-as-you-go basis, meaning there is really no upfront cost, and the cost for using the service is a lot cheaper compared to an on-premises environment.
There are many types of security services available but some of them are widely used by AWS, such as:
AWS IAM (Identity and Access Management) is a crucial service that enables you to securely manage access to AWS resources. By using AWS IAM, you can create and manage users, groups, and permissions, helping to ensure that only authorized individuals have access to your AWS environment. For beginners, understanding AWS IAM is essential for controlling access to resources and maintaining security in your cloud infrastructure.
IAM stands for Identity and Access Management. It refers to the policies and technologies used to ensure that the right individuals have the appropriate access to technology resources.

Overall, IAM is critical for maintaining the security, integrity, and efficiency of an organization’s IT resources.
IAM (Identity and Access Management) works through a combination of processes, technologies, and policies that help manage user identities and control access to resources. Here’s a breakdown of how IAM typically functions:
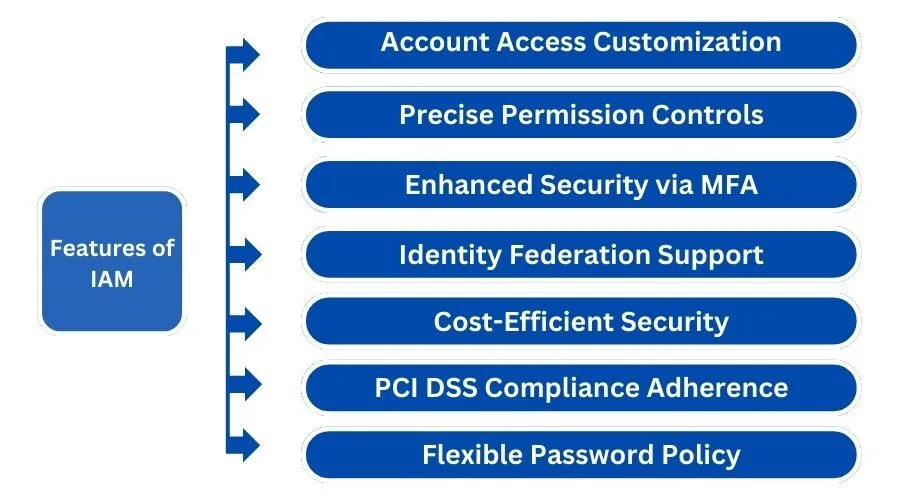
By combining these components, IAM provides a comprehensive framework for managing user identities and controlling access to sensitive resources, thereby enhancing security and operational efficiency. When setting up AWS IAM, it’s important to follow best practices such as enabling Multi-Factor Authentication (MFA) for all users. As you get more familiar with AWS IAM, you’ll be able to utilize roles, policies, and permissions to customize access levels for different users and services. Learning AWS IAM not only helps secure your AWS account but also plays a key role in managing large-scale environments with multiple users and complex access requirements.
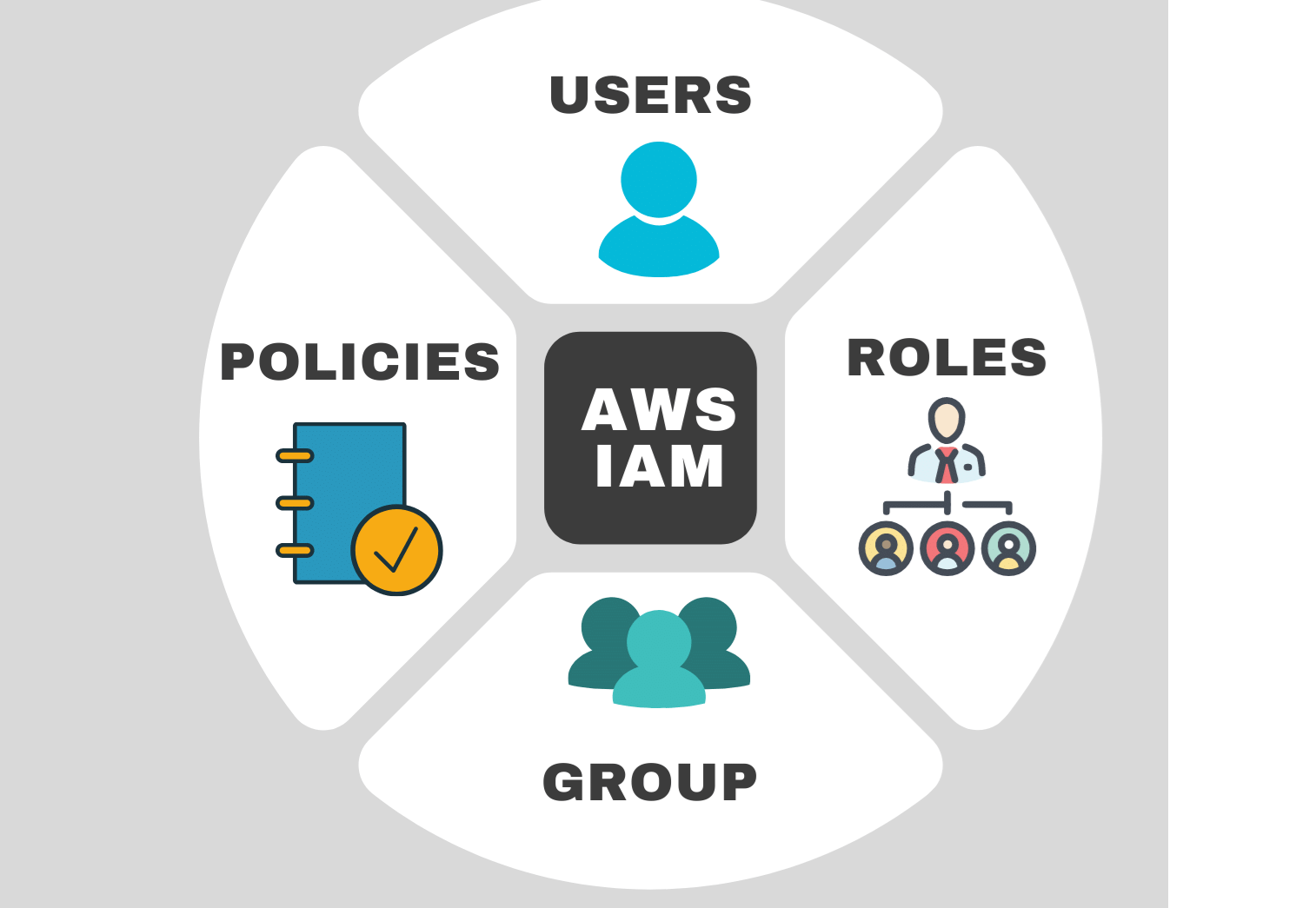
Definition: An IAM user is an entity that you create in AWS to represent a person or application that interacts with AWS resources.
Characteristics:
Definition: A user group is a collection of IAM users.
Characteristics:
Definition: Policies are documents that define permissions and are written in JSON format.
Characteristics:
Definition: An IAM role is an AWS identity with specific permissions that can be assumed by trusted entities (users, applications, or services).
Characteristics:
Confused about our certifications?
Let Our Advisor Guide You