Enroll Now and Get Upto 30% Off
* Your personal details are for internal use only and will remain confidential.

Last updated 24/02/2025
ISO 27001 is one of the foremost international standards that focuses on information security. It's been developed to help industries of any size. It contributes to protecting the data of businesses systematically and cost-effectively with the help of the adoption of an information security management system.
The ISO framework is a combination of different standards for businesses to use. It is part of a set of standards implemented to handle information security in the ISO/IEC 27000 series. It’s a well-known extension of all the ISO norms. This is because it provides the basic tool for managing data security chances to a rundown of ISO 27001 security controls, which are used to enhance the security of data resources. To get to know different factors about this, you must visit our ISO 27001:2022 Lead Auditor Certification Training Course.
Additionally, security objectives ensure that these controls align with risk management goals and compliance requirements. Companies aiming to strengthen their ISO 27001 compliance and cybersecurity position should zero in on ISO 27001 risk evaluation and smart control rollout. This guide will help you find your way through the ins and outs of ISO 27001 certification making sure you have a strong security management system. To get professional know-how in using these controls well, think about training courses from Novelvista, a top provider of security certification programs.
Annex A of ISO/IEC 27001:2022 is a reference list of 93 security controls designed to help organizations manage information security risks effectively. These controls are categorized into four areas:
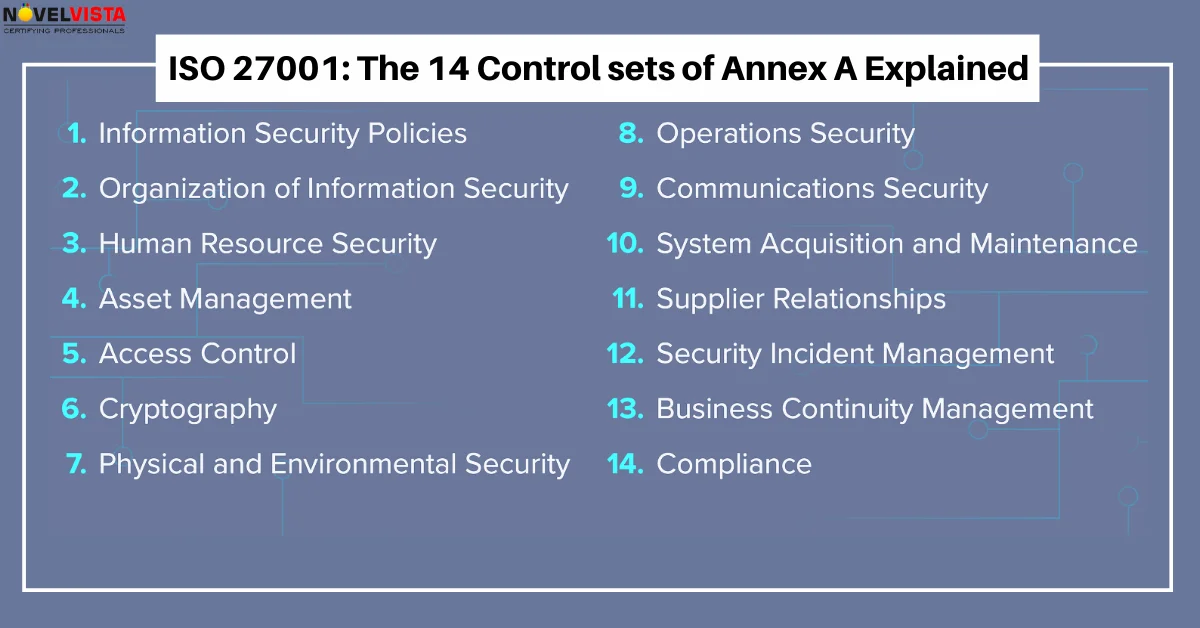
ISO 27001 Annex A controls are a set of security best practices designed to protect an organization's information. They are grouped into different categories to cover various aspects of information security. Here’s a simple explanation of these controls:
Annex A of ISO/IEC 27001:2022 has 4 domains (also called themes or sections). These domains contain a total of 93 security controls. The 4 domains are:
This is a change from the 2013 version, which had 14 domains and 114 controls. The 2022 revision has streamlined and consolidated some controls while introducing new ones to address modern security challenges.
Annex A.12: Operations Security stands as a super important part of ISO 27001. It makes sure companies set up tough security steps to protect their information systems. Inside this area, you'll find 14 controls tackling the big parts of IT work, system handling, keeping an eye on security, and guarding against online dangers. Keeping tabs on operations security is mega important for stopping trouble like data leaks, folks getting into systems they shouldn't have nasty software attacks, and computers crashing. Companies have got to be on their toes watching what goes on, making sure everything's set up safely, and keeping things running smoothly.
Organizations must develop and implement procedures that ensure secure IT operations. This includes establishing standardized guidelines for system usage, configuration, and maintenance.
Secure operations require:
To safeguard against cyber threats, organizations must implement anti-malware solutions and proactive security measures.
These include:
Comprehensive security monitoring is essential to detect and respond to security incidents Effectively.
This involves:
A robust backup strategy ensures business continuity in case of cyber incidents or system failures.
Organizations must:
Organizations must proactively identify and address vulnerabilities within their IT infrastructure.
Effective vulnerability management includes:
Developing and maintaining secure systems is crucial for ensuring long-term security resilience.
Best practices include:
To prevent unauthorized data exfiltration, organizations should implement:
The ISO 27001:2022 revision introduced key changes to Annex A controls, reducing the number of controls from 114 to 93 and organizing them into four new themes:
For professionals looking to stay ahead, enrolling in ISO 27001 Certification programs can provide in-depth knowledge and hands-on implementation experience.
It is up to each association to determine which ISO 27001:2022 controls they find relevant and implement them based on their assessment of the risks they face. The rest are reported to be non-material.
The rest are announced to be non-material, such as controls that are outsourced; improvement can be set apart as non-material if any business doesn’t redistribute the advancement of programming. The principle standard for selecting the controls is through hazard on the board, which is categorized in statements 6 and 8 of the fundamental piece of ISO 27001.
Also, the 5 fundamental piece of ISO/IEC 27001 expect you to characterize duties regarding dealing with those controls, and condition 9 expects you to quantify if the controls have satisfied their motivation. At long last, statement 10 expects you to fix whatever isn’t right with those controls and to make sure that you gain data security targets with those controls.
ISO 27001 is the international standard focused on information security. ISO 27001:2022 controls are recognized international standards published through the ISO and IEC. The standard specifies the requirements for developing and maintaining an effective ISMS to safeguard against information security risks.
ISO 27002 is the supplementary standard concentrating on information security controls that businesses might choose to develop. The ISO 27001 controls list includes the controls that you will see information security experts mostly refer to when discussing information security controls. Although Annex A ISO 27001 outlines each control in one or two sentences, ISO 27002 commits an average of one page per control.
As Annex A of ISO 27001 doesn’t give massive insights into each control, there isn’t typically one sustenance for each control that brings you the thought of what you have to accomplish. This is the reason ISO 27002 was distributed. Make sure to check our ISO Lead Auditor Combo Certification to learn more about this in detail.
There are some things regarding Annex A as it brings you the ideal review of which controls you can apply, so you remember some that would be significant. It paltrovides you with the adaptability to pick just the ones you discover appropriate to your business, so you don’t need to spend assets on the ones that are not relevant to you.
Implementing Annex A controls requires a strategic approach. Below are some best practices:
Organizations should tailor Annex A controls based on their risk assessment and security needs. The controls should align with:
Our ISO 27001:2022 Lead Auditor Certification Training Course provides you with various benefits, such as follows:
Having an in-depth understanding of ISO 27001 controls list Excel might be crucial for businesses that aim to develop a robust information security management system. Through this blog, the details of Annex A bring the in-detailed set of controls that contribute to addressing different aspects of information security. Every individual control is designed to reduce the specific risks and provide security, integrity, and availability of information assets. With the help of focusing on Annex A controls, businesses can gain insights into the essential measures that are needed to protect sensitive information. From security policies and asset management to access control, cryptography, and incident response, the control covers a wide range of areas that focus on having a robust and secure information security framework.
Furthermore, this blog also focused on elaborating on the requirement of aligning the controls to suit the business context by considering factors such as industry, size, and risk appetite. It’s important to conduct a comprehensive risk assessment and develop controls that address risks successfully. Developing the ISO 27001 2022 controls list Excel elaborates the commitment to information security best practices. It also helps to develop trust among stakeholders, including customers, partners, and regulatory bodies. In conclusion, businesses attempting to develop a strong information security framework must have a solid grasp of ISO 27001 Annex A controls. Organizations may reduce risks, safeguard their priceless information assets, and promote an information security excellence culture by utilizing these controls effectively and tailoring them to their particular situation.
Topic Related PostVikas is an Accredited SIAM, ITIL 4 Master, PRINCE2 Agile, DevOps, and ITAM Trainer with more than 20 years of industry experience currently working with NovelVista as Principal Consultant.
* Your personal details are for internal use only and will remain confidential.